Project Description

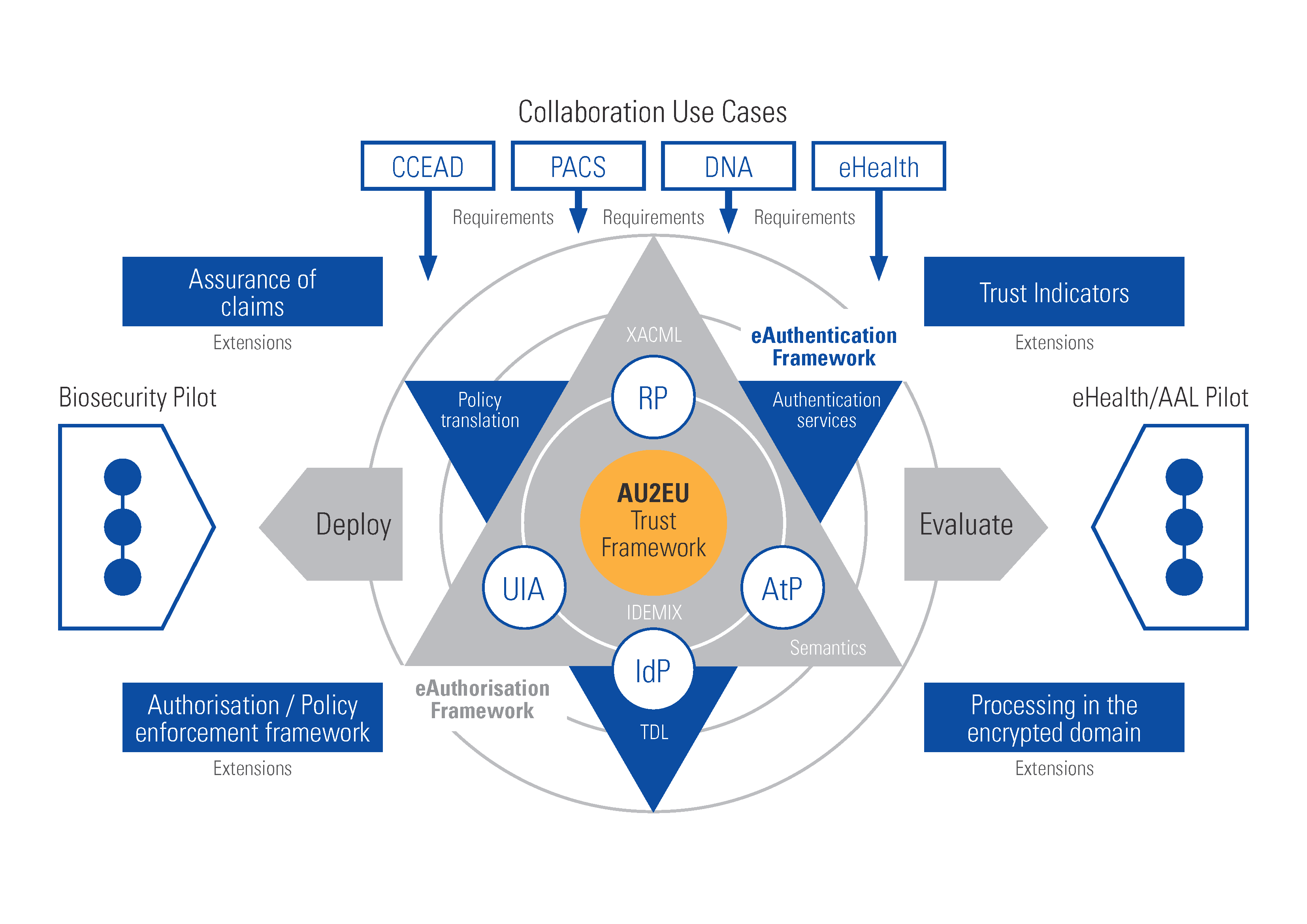
The aim of the AU2EU project is to implement and demonstrate in a real-life environment an integrated eAuthentication and eAuthorisation framework to enable trusted collaborations and delivery of services across different organisational/governmental jurisdictions.
Consequently, the project aims at fostering the adoption of security and privacy-by-design technologies in European and global markets. This objective will be achieved by:
1) designing a joint eAuthentication and eAuthorisation framework for cross-domain and jurisdictional collaborations, supporting different identity/attribute providers and organizational policies and guaranteeing privacy, security and trust;
2) advancing the state-of-the-art by extending the joint eAuthentication and eAuthorisation framework with assurance of claims, trust indicators, policy enforcement mechanisms and processing under encryption techniques to address specific security and confidentiality requirements of large distributed infrastructures;
3) implementing the joint eAuthentication and eAuthorisation framework as a part of the platform that supports collaborative secure distributed storage, secure data processing and management in the cloud and offline scenarios;
4) deploying the designed framework and platform in two pilots on bio-security incident management and collaborative services in Australia and on eHealth and Ambient Assisted Living in Europe; and
5) validating the practical aspects of the developed platform such as scalability, efficiency, maturity and usability.
Privacy-Preserving Management of DNA Data
Recent advances in DNA sequencing technologies have attracted considerable attention from the healthcare domain, since healthcare applications can use complete DNA sequences in order to provide diagnoses, personalized medical treatments and even personalized drug design. Medical research, diagnostics and treatment that are based on genomic data, however, require not only access to DNA data and collaboration between different parties such as pharmacies, sequencers, researchers and patients, but also intensive computational resources. To support such collaborations, distributed, (possibly cloud-based) DNA archiving systems, similar to PACS, become a necessity. Remarkably, DNA data are self-identifying sensitive data meaning that they are a unique identifier of human beings that contain information used for disease risk profiling, ancestry determination and, potentially, other more personal physiological aspects. Therefore proper access management in distributed DNA-systems needs to be built on an advanced Authentication and Authorization framework, that also supports a combination of policy-based access control with more sophisticated techniques to protect DNA data.
In AU2EU project we study the problem of storing and sharing genetic data for its further analysis while at the same time protecting the privacy of the underlying data. Given that the data is unique and inherited, information theoretic security is a desirable property for genomic data protection. Therefore we will study generative statistical modeling of genetic sequences applied to functional comparison of genetic sequences. Furthermore, we will develop information-theoretic framework to analyze and characterize privacy-preserving properties of these models.
Cryptographic Policy Enforcement
Regulating access to data in large distributed systems becomes a central problem while establishing trusted collaborations. One of the promising modern access control mechanisms make use of cryptographically enforced access control. Here policies are enforced using cryptographic primitives. In this approach the server is assumed to be honest-but-curious, meaning that it stores all the data correctly and follows all the protocols, but tries to learn the data. Therefore the idea here is to map a policy associated with data to a cryptographic key and then encrypt the data using this key. The encrypted data can then be stored on the server, and the user can be assured then that only the party that has the right decryption key can access the data.
In AU2EU project we will study advanced asymmetric-key encryption schemes such as attribute-based encryption (ABE) schemes, and will investigate how the ABE schemes can be designed to support semantic mapping of attributes, policy updating, key revocation and dynamicity of distributed virtual collaborations that allow other organizations to join and leave such collaborations without the need to re-encrypt the data in the system.
Results and Publications
L. Kusters and T. Ignatenko, “Context Trees for Privacy-Preserving Modeling of Genetic Data”, in Proceedings of 2016 International Zurich Seminar on Communications (IZS), March 2 - 4, 2016, Zurich, Switzerland
L. Kusters and T. Ignatenko, “DNA sequence modeling based on context trees”, in Proceedings of the 36th WIC Symposium on Information Theory in the Benelux and the 5th Joint WIC/IEEE Symposium on Information Theory and Signal Processing in the Benelux, May 6-7, 2015, Brussels, Belgium, (pp. 96-103). Brussel: ULB.
T. Ignatenko and M. Petkovic, “Privacy-Preserving Matching of DNA Sequences”, in Proceedings of Workshop in Information Security Theory and Practice (WISTP2014), Heraklion, Crete, Greece, June 30-July 2, 2014, pp.180-189. LNCS 8501
M.Asim, M. Petkovic, T. Ignatenko, “Attribute-based Encryption with Encryption and Decryption outsourcing”, in Proceedings of 12th Australian Information Security Management Conference, 2014 SRI Security Congress, Security on the Move, December 1-3, 2014, Perth, Western Australia
Partners
TU Eindhoven, The Netherlands (Coordinator)
Philips Electronics B.V., The Netherlands
Bicore Services B.V., The Netherlands
NEC Europe LTD,Germany
IBM Research GMBH, Switzerland
German Red Cross E.V., Germany
Thales Communications & Security SAS, France
Commonwealth Scientific and Industrial Research Organisation (CSIRO), Australia
Edith Cowan University (ECU), Australia
Royal Melbourne Institute of Technology (RMIT University), Australia
University of New South Wales (UNSW), Australia
Macquarie University, Australia











